Introduction to Roles and Permissions
Enterprise applications are rarely collaborative with multi-role users, and each role has different operational privileges on enterprise data. The application's privilege configuration is already very granular and can be custom configured to enable different users with different operational privileges.
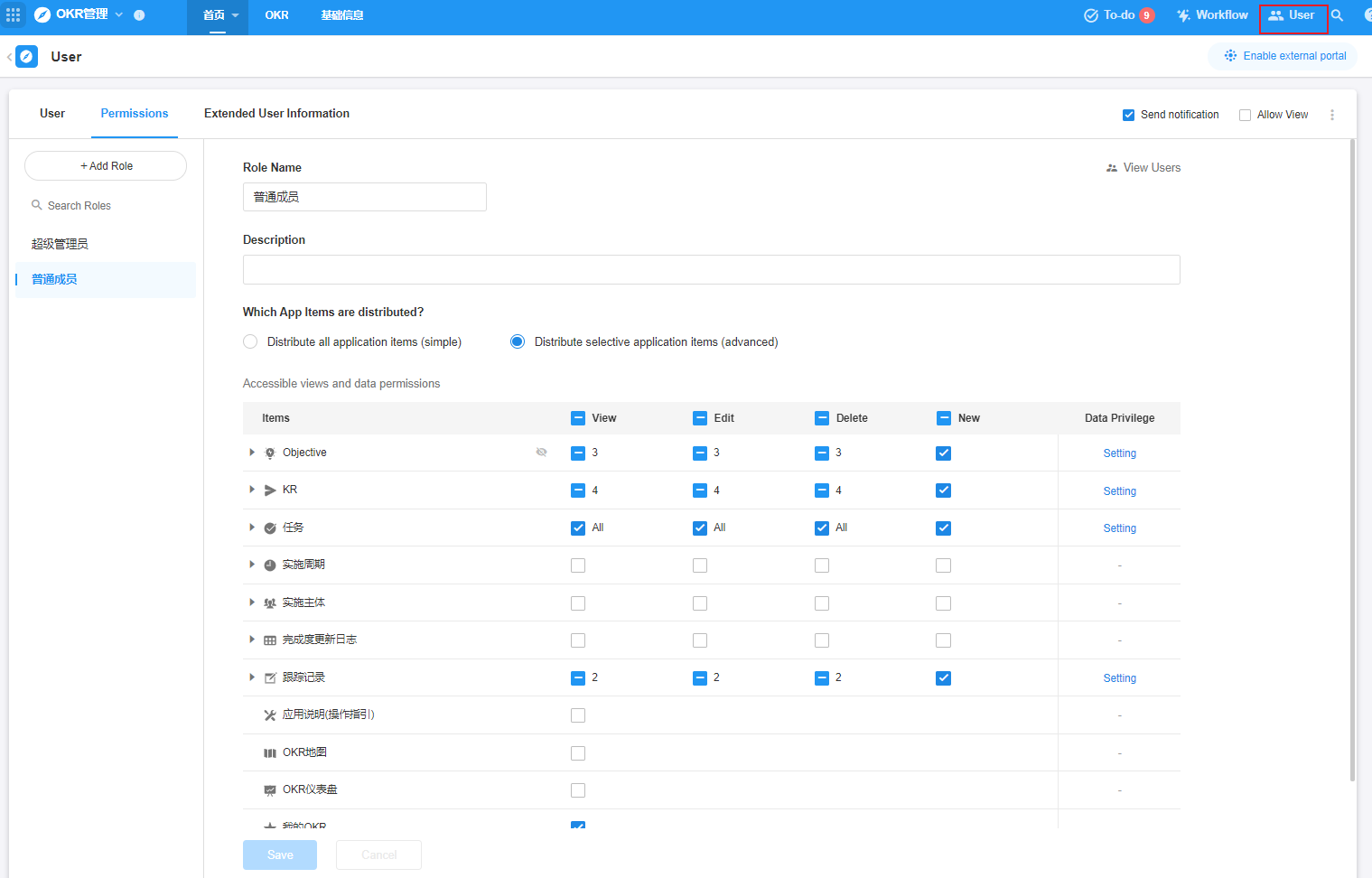
User's permission configuration logic
User permissions are associated with roles, where operational permissions are first configured for a role, then the role is given to the user, and the user gets the permissions for those roles by becoming a member of the appropriate role. Such a permission design (RBAC design thinking) is clear and easy to manage.
The following kinds of permission requirements can be achieved through the configuration of role permissions:
- There are multiple worksheets under the application, and users can only see the specified worksheet.
- There are multiple views under the worksheet, and users can only see the specified view.
- There are many data under the view, and the user can only view the data he created.
- The user can view all the data, but can only modify/delete their own related data.
- When users view a row of records, some fields are hidden.
- When users edit data, but some fields can be edited, some fields are not editable.
- When users add a new row of records, they can only fill in the contents of certain fields.
- When users are viewing, they cannot share, print, etc.
Have questions about this article? Send us feedback